-
![]() ESG in bankingESG-conscious banking should create new and future-proof value streams to build a sustainable and resilient business.Read More
ESG in bankingESG-conscious banking should create new and future-proof value streams to build a sustainable and resilient business.Read More -
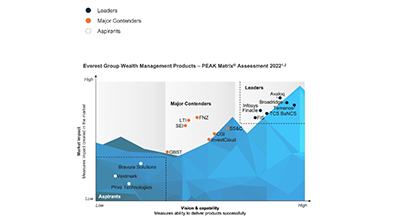
![Everest Group PEAK Matri Everest Group PEAK Matri]() Everest Group PEAK MatrixA comprehensive solution delivering a full spectrum of wealth products as great experiences. It also improves the productivity of financial advisors and streamlRead More
Everest Group PEAK MatrixA comprehensive solution delivering a full spectrum of wealth products as great experiences. It also improves the productivity of financial advisors and streamlRead More -
![]() Subsidiary of an American Bank in IndonesiaFind out how a leading American bank adapts to a digitalized trade and supply chain finance operations as a part of its larger transformation by leveraging Finacle Trade Finance Solution Suite.Read More
Subsidiary of an American Bank in IndonesiaFind out how a leading American bank adapts to a digitalized trade and supply chain finance operations as a part of its larger transformation by leveraging Finacle Trade Finance Solution Suite.Read More
-
![]() Recomposing Banking: Leading the Digital ContinuumReport gives you a glimpse of the major areas where recomposing banking will create significant impact and value, Infosys Finacle has put together a report on..Read More
Recomposing Banking: Leading the Digital ContinuumReport gives you a glimpse of the major areas where recomposing banking will create significant impact and value, Infosys Finacle has put together a report on..Read More -
![]() Core Banking on Cloud: Navigating to the Fast LaneTake a deep dive into cloud-based core banking and explore the imperatives, opportunities and challenges, and the hallmarks of a robust solution.Read More
Core Banking on Cloud: Navigating to the Fast LaneTake a deep dive into cloud-based core banking and explore the imperatives, opportunities and challenges, and the hallmarks of a robust solution.Read More -
![]() Embracing Payments ComposabilityA step-by-step guide for maximizing Real Time Payment opportunities by embracing Payments Composability...Read More
Embracing Payments ComposabilityA step-by-step guide for maximizing Real Time Payment opportunities by embracing Payments Composability...Read More
-
![]() Shaping Banking’s Next: Banking Technology Trends for 2025 and BeyondThe banking industry has been balancing disruption and opportunity for several years now, and the pace of change shows no signs of slowing as we move into 2025 and beyond.Read More
Shaping Banking’s Next: Banking Technology Trends for 2025 and BeyondThe banking industry has been balancing disruption and opportunity for several years now, and the pace of change shows no signs of slowing as we move into 2025 and beyond.Read More -
![]() Virtual Accounts 2.0: Surpass Conventional Cash Management and Unlock Next-Gen PossibilitiesVirtual Account Management was a groundbreaking shift in the banking landscape, revolutionising use cases like cash concentration, pooling, centralised treasury management, and in-house banking (POBO, ROBO, COBO)Read More
Virtual Accounts 2.0: Surpass Conventional Cash Management and Unlock Next-Gen PossibilitiesVirtual Account Management was a groundbreaking shift in the banking landscape, revolutionising use cases like cash concentration, pooling, centralised treasury management, and in-house banking (POBO, ROBO, COBO)Read More -
![]() Unlocking Hybrid CloudAs banks push forward with their digital transformation agenda, cloud serves as a pivotal enabler. Each bank, at varying stages of adoption, crafts its unique path, dictated by context, regulations, and risk appetite.Read More
Unlocking Hybrid CloudAs banks push forward with their digital transformation agenda, cloud serves as a pivotal enabler. Each bank, at varying stages of adoption, crafts its unique path, dictated by context, regulations, and risk appetite.Read More
-
![]() Banking on CloudThis report from Infosys Finacle delves into the need for accelerating cloud adoption, highlights the current state of the industry, and puts forth key recommenRead More
Banking on CloudThis report from Infosys Finacle delves into the need for accelerating cloud adoption, highlights the current state of the industry, and puts forth key recommenRead More -
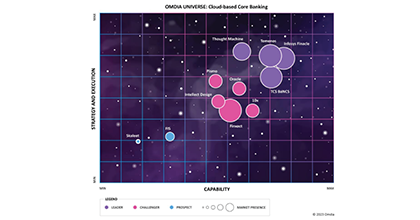
![]() Omdia Universe | Cloud-based Core BankingIn the report, Omdia highlights the following key capabilities of leading cloud-based core banking providers:Read more
Omdia Universe | Cloud-based Core BankingIn the report, Omdia highlights the following key capabilities of leading cloud-based core banking providers:Read more
-
![]() Emirates NBDEmirates NBD consolidates its operations on a single version for scalability, agility, and standardization.Read More
Emirates NBDEmirates NBD consolidates its operations on a single version for scalability, agility, and standardization.Read More -
![]() A Global Top 5 BankDiscover how a global top 5 bank headquartered in the US accelerated payments transformation.Read More
A Global Top 5 BankDiscover how a global top 5 bank headquartered in the US accelerated payments transformation.Read More -
![]() Union Bank of IndiaUnion Bank of India launches Union Virtual Connect (UVConn) by leveraging WhatsApp to provide customers personalized banking services.Read More
Union Bank of IndiaUnion Bank of India launches Union Virtual Connect (UVConn) by leveraging WhatsApp to provide customers personalized banking services.Read More

Personal Data Everywhere?
Blogs
Early morning, I received a call on my cell phone from a consumer finance company explaining to me some consumer finance/EMI offers. After a few hours, I received a call from one call center of a bank selling credit cards about life time free card with other offers. In the afternoon, I received a call from an Insurance company about some insurance offers and insurance tied with investments. These are a few calls each one of us typically receives on a daily basis. I don’t consider myself to be a high net-worth individual/very important person/person in the public domain to be receiving these calls so often. Obviously I have not registered myself in the “do not call” registry website and immediately felt the need to do it.
In the afternoon, I checked on to a web site of a travel company provider to look for some options for travel during holidays and these were very casual checks, not planned ones. When I went to another site using the same laptop/IP address, immediately popups for travel destinations I had looked up earlier appeared. Yet another instance was while trying to make a mobile payment – checking the quick payment options on a google engine search returned multiple results about relevant websites. I tried opening a website I had visited earlier and immediately my mobile number and mobile account number popped up without any registration or login. Since the earlier payment was through credit card, the entire credit card information except for CVV was auto-populated into the screen though I have not enabled autofill or saving of credit card data on any sites I visit. Though CVV is captured in encrypted format and credit card payments are further authenticated using multi-factor authentication techniques, this is still a grave concern to me.
There are other sites where one registers for making purchases/online shopping/ecommerce and the access could be browser based or through mobile. In most of these sites, apart from name and e-mail address, mobile numbers, residential address with PIN and other credentials are given. There is also an increasing tendency to source PAN details, Aadhar, KYC or other forms of identity details relevant to country which are shared for completing the registration process/formality. There is also a message to comply with KYC guidelines asking for mandatory documents to register users on many online shopping /establishments. In the urgency to complete the registration, we tend to furnish this information in an ad hoc manner without a recheck. People are also lured by the freebies /discounts being offered through the ecommerce platform for a particular event and are not sensitized by the confidential personal information being captured/shared.
A few social media sites are mediums where data once used/searched by an existing user gets stored and in seconds, the search data is shared or used by multiple other websites for sourcing some other information. Needless to say, there is an analytical engine running over these sites which enables collection of the data, analysis of the data, tracking the IP address and the next time when the user logs into a website it surprises them with the information one is searching. There is also a tendency to upload photographs/images, update of status by an individual for important events like birthday celebrations, awards and ceremonies or important places visited which could be misused.
The mobile numbers are possibly shared by service providers/agents of the companies to different sources with/without a fee. The data on mobile numbers possibly gets extracted secretly, gets shared with other like-minded companies and is used for calling purposes. Personal data is available on mobile/laptop and used/shared through the network making the data really vulnerable.
The extent of data that is tied to or associated with mobile/credit card/PAN/Aadhar is enormous. Some of the data may not be known to immediate family members but might be available to a select set of vendors/company, and is potentially at the risk of getting compromised for malicious intent.
The EU parliament approved the GDPR (General data protection regulation) in 2016 to harmonize data privacy laws across Europe, and to protect and empower the citizen’s data privacy. However, this is in a very early form and all citizens across the globe are susceptible to data theft/attacks/breaches in cyber world currently. It will take time to have laws framed in terms of controlling the data, sharing the data, protecting the data, using the data, processing the data and till that time, it is up to the individual to safeguard to the extent possible.
To conclude, with digitization and communication revolution rampant across the globe, an individual is vulnerable to a data threat/piracy of personal information – mobile number, card number, identification details, bank account number (in a few rare cases) and the like. Though there are in-built security measures for accessing sites and for conducting financial transactions that may require multiple authentication modes, the threat still looms and one needs to be wary of the information being shared in the cyber space. Till cyber security and protection reaches a stage of maturity where there is a collective rule/regulation encompassing the devices and websites with technology assistance for controlled data sharing and processing across countries/geographies, it is up to the individual to ensure adequate measures in using/sharing personal data over the web.


©2025 -Edgeverve Systems Limited | All rights reserved